Azure Virtual Network Peering
Secure connection over private endpoint from a peered virtual network
Preface
Azure provides multiple options to have a secure n/w connection across PaaS resources and in this article, let's go over Virtual Network peering which allows secure communication across resources in different virtual networks.
What is Virtual Network Peering
Virtual Network peering allows seamless connection between Azure Virtual Networks. It's a very common practice to have multiple virtual networks to have logical/physical grouping of Azure resources. Virtual Network pairing thus enables the network connection across peered VNet(s) to use Microsoft's private backbone network and hence is more secure and reduces latency.
Virtual Networks can be paired,
Regional - When VNets in the same region are paired
Global - When VNets in different regions are paired
If the virtual network is across different resource groups and subscriptions, Resource IDs are used to add VNet peering
The IP address space of the peered virtual network should not overlap. The connection will not be established across the network in such a case.
Prerequisites
Active Azure Subscription
Basic know-how to setup CosmosDB and Azure Function
Reference to the previous Article that explains CosmosDB Setup and Azure Function setup
Access CosmosDB from a peered virtual network
In the previous article, we could see the connection from Azure Function to Azure CosmosDB using a Private endpoint. Would recommend reading that post as this article is an extended means to connect from a different virtual network.
Virtual Network Setup
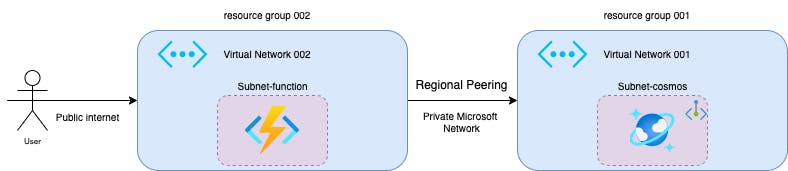
Create two virtual networks and add a peering between both virtual networks
Virtual Network I
Add a Virtual Network let's say VNet-001 in a resource group.
Add a subnet-cosmos to use while adding a cosmos DB private endpoint.
Virtual Network II
Add another Virtual Network. This can be added to a new resource group or it could be created in the same RG as we have the PaaS resource. In this example, I have added Virtual Network 002 in a different resource group to show region peering.
Add two subnets,
subnet-cosmos which will be used to create a private endpoint in the CosmosDB
subnet-function, subnet to restrict the outbound connections from the azure function
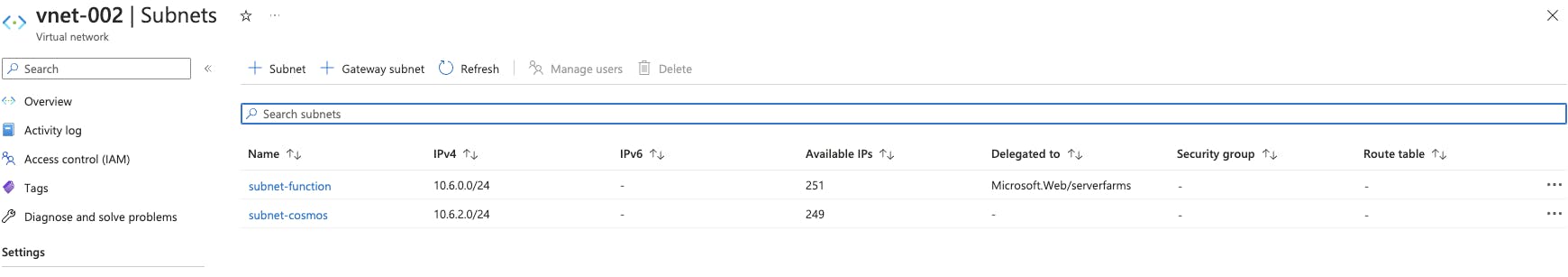
Vnet Peering
1. Click Peerings under settings and click Add
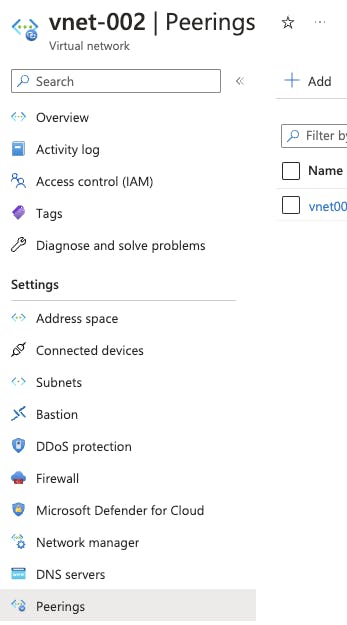
2. In the next window, create Virtual Network Pairing
1. Create a peering link name, here you could see two peerings being created. This creates peering from both networks involved here
2. You could control inbound and outbound traffic flow across the peering network
3. You could add a gateway if the peered network connections are managed by a gateway. This is outside the scope of this article and not covered, hence leave it default.
4. Azure provides an option to create a Peering with the Resource ID. Assuming that the Virtual Network is managed by a different team and under a different governance model, the peering could still be established with the resource ID. In this example, since we manage both virtual networks, choose the peer network and click add.
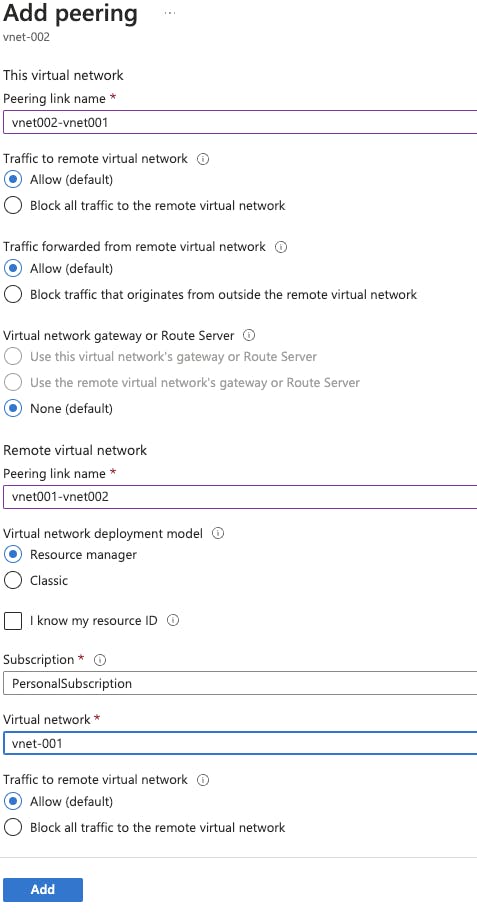
Azure CosmosDB
Add an Azure Cosmos DB and set up a private endpoint. Private endpoint creates Private DNS zone for domain name resolution
Add an Azure CosmosDB and a sample database and a sample collection
You could add a Private Endpoint while creating a CosmosDB or later using the Networking tab in the resource
Disable public and Azure portal access to the resource
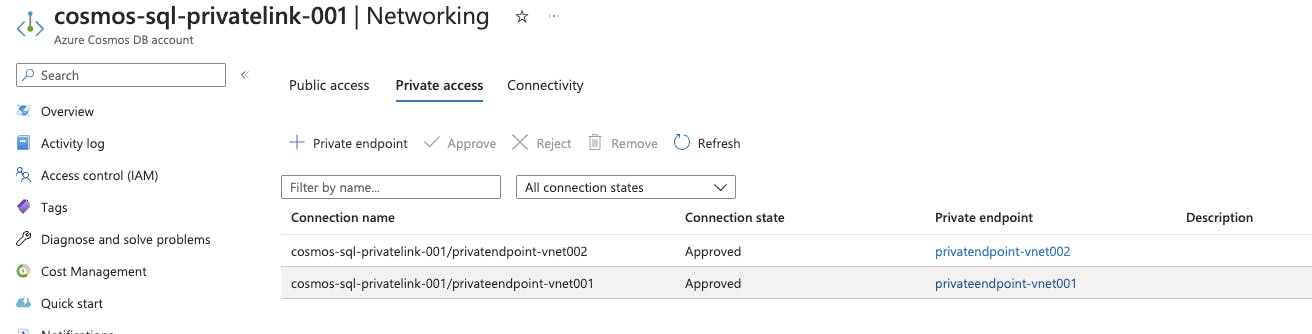
Add two Private Endpoints one for each of the subnet-cosmos in each virtual network
Azure Creates Private DNS by default while adding a private endpoint**,** which helps in resolving FQDN and DNS aliases within the virtual network. This gives a uniform address resolution for the configured resources. Private endpoints assign an IP within the virtual network subnet and the DNS zone helps in the domain name resolution.
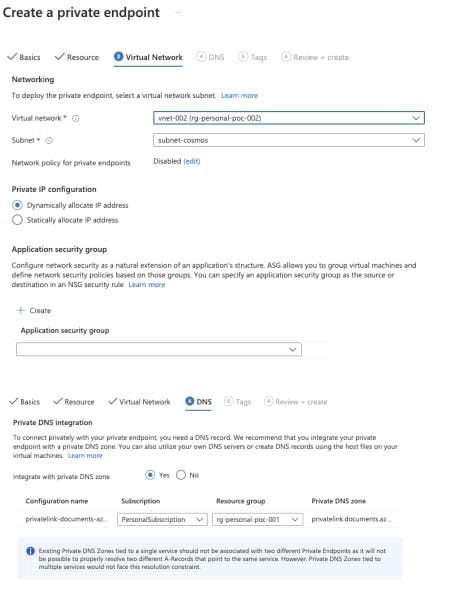
Here, I have chosen an existing Private DNS Zone that is created in Resouce Group 001
Private DNS Zone and Virtual Network Links
Link Virtual Network 002 as a virtual link in the private zone. This enables the resolution for connection from the peered virtual network i.e. Vnet 002 in this example.
A Virtual Network Link allows you to link your Private DNS Zone to one or more Virtual Networks, enabling DNS resolution across Virtual Networks within the same Azure region. This association is done by creating a Virtual Network Link, which enables the Private DNS Zone to be resolved from within the linked Virtual Networks.
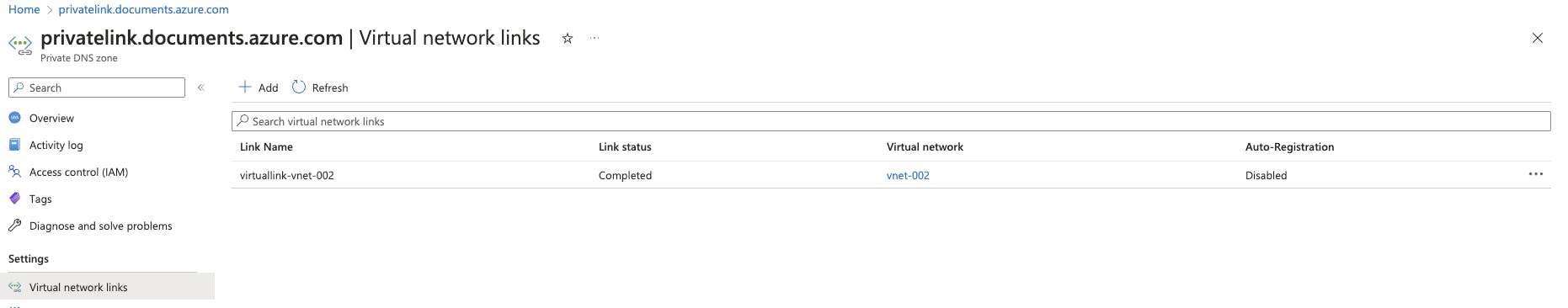
I have created a Virtual link in the Private DNS Zone ( in the resource group 001).
You can either give the Virtual Network Resource ID or choose the Virtual Network when you add a link. This is the end state after adding a virtual link.
Azure Function
Created a sample Azure function, and used Azure Function VS Code plugin to deploy this as a function app into Azure. Ensure to add a local settings file with the appropriate CosmosDB connection string.
This plugin by default deploys to a free tier App Service Plan. We may have to create an Azure App Service with a minimum B1 tier (which supports networking options) and use the same when prompted while using the plugin in the VS Code
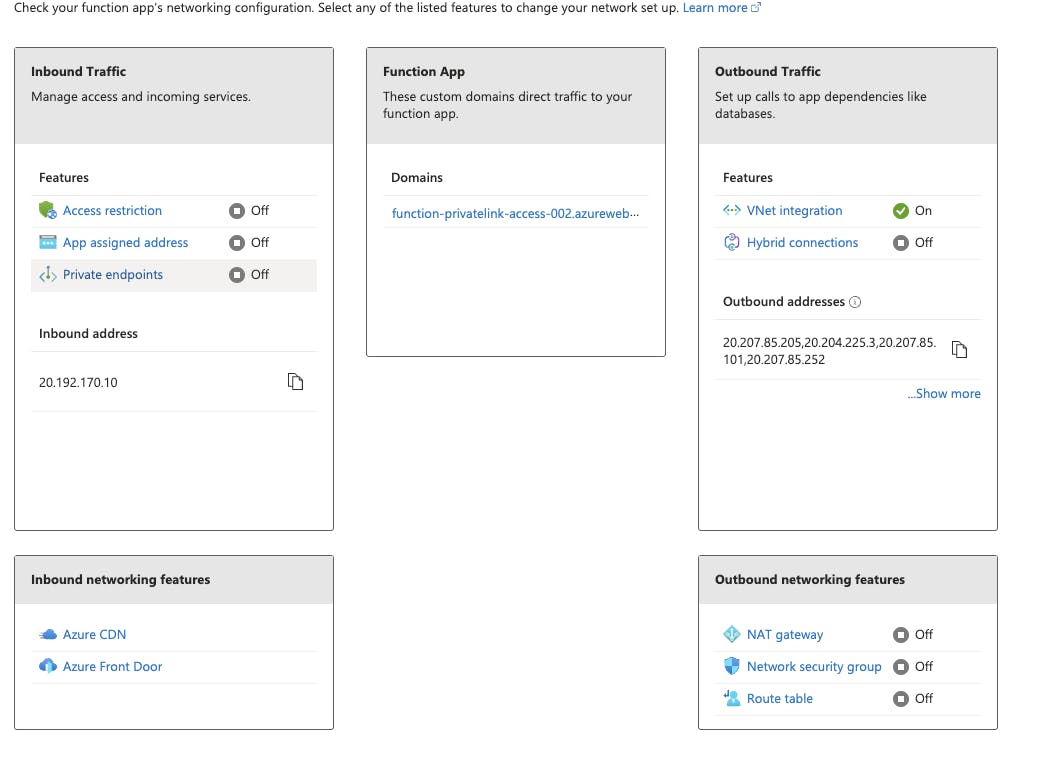
Once the function app is deployed into Azure, use the networking tab in the function app to set inbound and outbound connections
Click VNet integration in the outbound traffic and choose subnet function created under Virtual Network 002
Conclusion
We have so far,
Created virtual network peering across two Azure Virtual Network
Added subnets in each network and created a private endpoint in cosmos DB in a different resource group. Blocked public access to the database.
Created a virtual network link in the Private DNS zone to add the peered virtual network
Azure function network outbound traffic is restricted to a subnet in a primary virtual network.
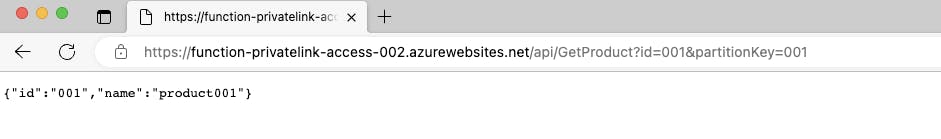
Testing the Azure function with the above settings
Voila ! .. We could successfully establish a peering and secure connection across Azure PaaS services in a different virtual network